By now, we all know the name “Snowden.” And, I’m sure, we all have opinions about what he did and exactly who he is -- be it hero or villain or maybe something in between. But in the world of data security, Snowden was a lot more than a piece of pop culture or a political phenomenon. He was a figure of what was already happening.
You see, for a really long time, when people thought about data and security, there was this weird little notion of some fenced-off perimeter keeping the “bad guys” out -- heck, that’s probably how most people still think of data and security. But for those on the inside or who just happened to be in the know, this was a pretty brash oversimplification of the problem.
The truth was (and still is) a lot of breaches come from within. And while Snowden wasn’t the first to pull off the infamous “inside job”, the fact that he did it to the most powerful data collection agency in the world really drove the point home. And look, I know, it’s tempting to say, “well, we all know how incompetent the government can be,” but the fact that these kinds of breaches have happened very publicly to some very big companies shows this isn’t some singular problem that can be explained away with “well, bureaucracy.”
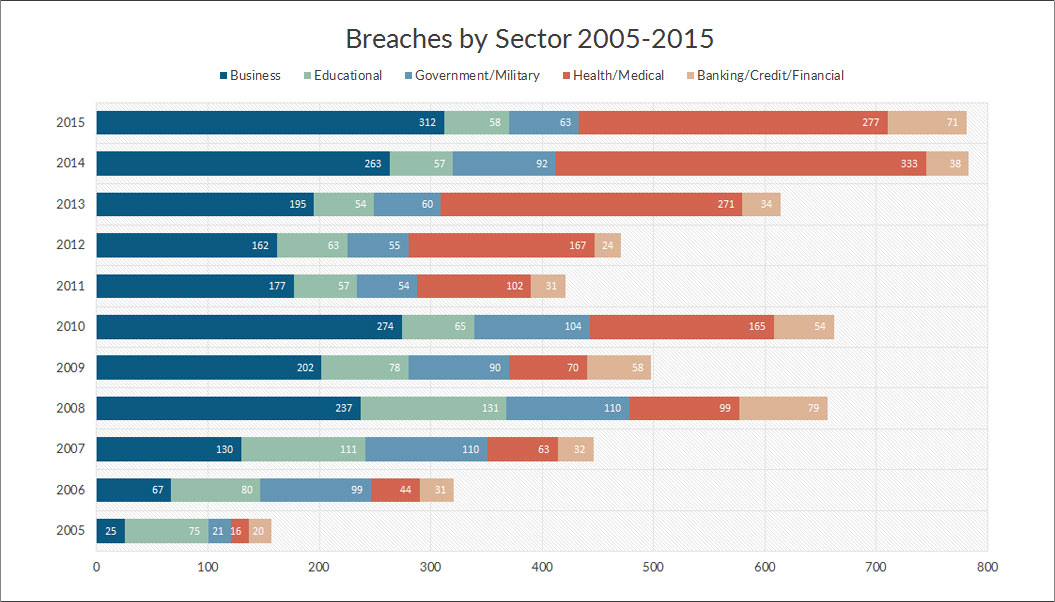
The reality is there’s just so much data -- multi-petabytes of it, in some cases -- and we’re really not doing the best job at keeping track of all of it. Well, we’re not doing the best job at three things, really:
Unifying it. - So, there are these things called data silos, and if you need the dictionary definition for them, they’re “separate database(s) or set(s) of data files that are not part of an organization's enterprise-wide data administration.” And just reading that, you can probably already spot the huge potential hazard they might pose -- namely, the part where you have huge repositories of data floating around in the nebulous unchecked.
Gartner.com actually predicted back in 2014 that in 2016, “more than 80 percent of organizations will fail to develop a consolidated data security policy across silos, leading to potential noncompliance, security breaches and financial liabilities.” And given the growing number of breaches these past two years -- not to mention, lawsuits -- they seem to have been onto something.
Scaling it. - Now, it’s one thing to unify your currently existing data, but that loses a lot of value as soon as new data starts coming in. The problem here is that most people don’t scale their storage and analysis of data, which leads straight back to the above scenario. In a perfect world, data should be able to be analyzed and accessed almost seamlessly within a time frame that makes sense.
Identifying when things get weird. - Imagine there’s someone moving out huge packets of confidential data to some unsecure silo. Now, this doesn’t necessarily mean that something malicious is going on -- they could be acting in error or worse, be the victim of a phishing scam -- but the end result is the same...potentially compromising huge chunks of sensitive data.
This is why mapping the normal transference of data and getting the right person on the phone when things get, uh, “phishy” is so important. It’s a bit of a challenge, but doable. And worth it.
The point, really, is that we need to rethink the way that we go about securing data. A recent study by McAfee found that 43% of all data loss was due to “internal actors”, and half of those were accidental. And unlike Snowden -- which most, I’d say, see as a case of whistleblowing -- the malicious ones aren’t as altruistic. 62% of that data stolen is private or personal information of customers, which is far more valuable these days than a simple credit card number.
And it doesn’t take much, as Latanya Sweeny, professor of Government and Technology in residency at Harvard, famously showed. In 2000, she was able to demonstrate that 87% of Americans can be individually identified by three things: a zip code, gender, and date of birth. So, basically, what you put down for a pizza delivery is enough to open up a floodgate of information if someone was so inclined.
This is truly an “enemy behind the gates” situation. In large institutions, at least, data will be compromised one way or the other. And the question we really should be asking isn’t how we can protect it...but how can we keep it from getting out?
Related Posts
Additional Resources
Data Consolidation During M&A
Melinda Watts-Smith, Global Head of Services at ZL, shares her insights on managing unstructured data in M&A. Drawing from her…...
The Rise of Full Content Management
Discover how the market is shifting towards full content management as a solution for file share governance....
The Problem With File Analysis Solutions
File analysis solutions promise to streamline data governance, enhance security, and optimize storage resources. However, the reality is not always…...